
Towards Trusted AI Week 17 – Prompt injections VS autonomous agents
Is this the year that AI breaks into our bank accounts? Dazed Digital, April 19, 2023 According to Alex Polyakov, the founder and CEO of Adversa AI, the security of ...
Adversarial ML Digest admin todayMay 3, 2023 38
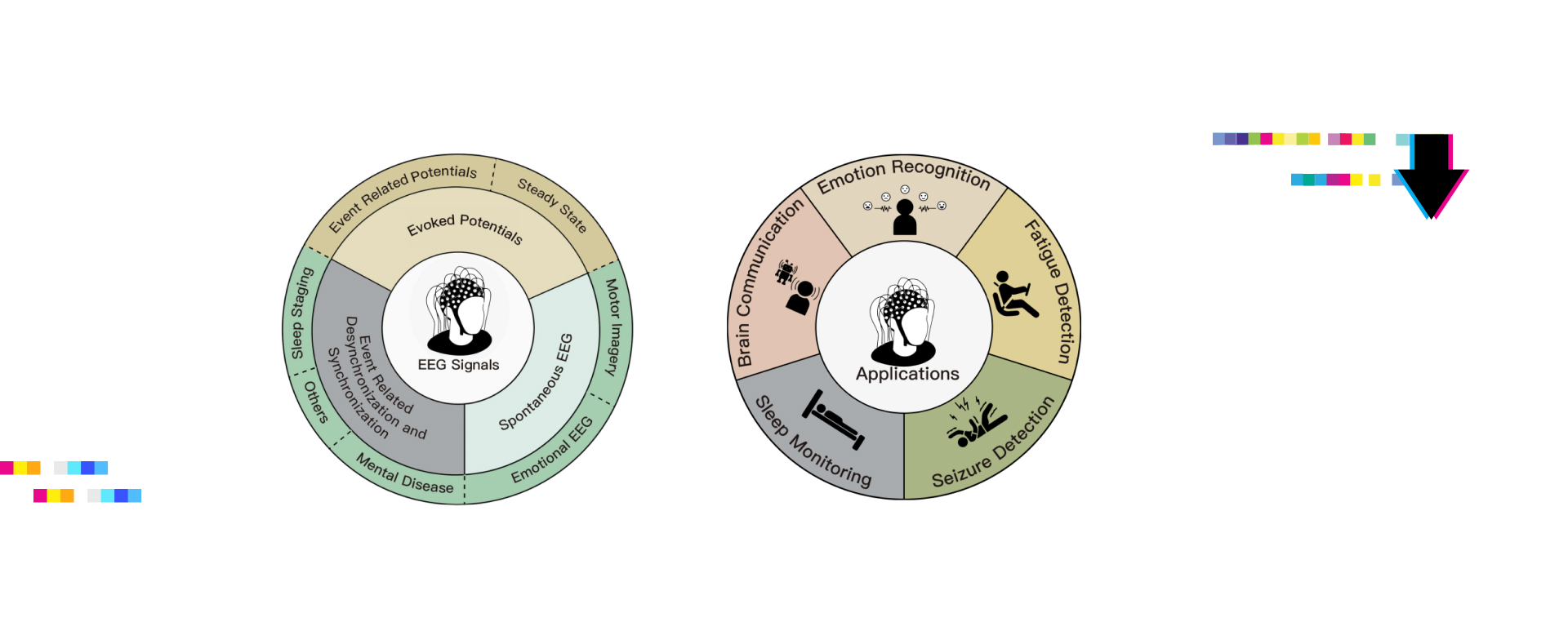
In an ever-evolving technological world, groundbreaking research in the fields of Artificial Intelligence (AI) and network systems continues to raise eyebrows and pique interests. These four cutting-edge Arxiv research papers touch upon the realms of search engines, EEG systems, dynamic networks, and privacy attacks on AI chatbots. Hold onto your seats as we delve into these striking pieces of innovation!
This research aims to exploit search engines through encoding-based attacks. What researchers did: The researchers designed an attack technique that leverages the encoding schemes of search engines to extract confidential data. They performed experiments by applying these attacks to various search engines. Results: The study revealed that the encoding-based attacks were successful in extracting sensitive data from different search engines. This form of attack was found to be efficient, as it bypasses the search engines’ security mechanisms. Feature and Contribution: This research uncovers a security loophole in search engines and paves the way for improving security measures by comprehending encoding-based attacks.
We further demonstrate that this attack is successful against LLM chat search including Bing’s GPT-4 chatbot and Google’s Bard chatbot.
The research aimed to survey the application of AI in EEG (Electroencephalogram) systems and enhance its interpretability and robustness. What researchers did: The researchers conducted an extensive survey of existing literature and works pertaining to AI applications in EEG systems. They then focused on the challenges and solutions regarding the interpretability and robustness of AI in EEG. Results: The study showcases various AI techniques in EEG systems and highlights the issues related to their interpretability and robustness. It provides insights into potential solutions for these issues. Feature and Contribution: The paper offers a comprehensive overview of the application of AI in EEG systems, which can be valuable for researchers and practitioners working on brain-computer interfaces and neuroscience.
The study aims to develop an adversarial attack technique targeting AI models deployed in dynamic networks. What researchers did: Researchers designed GradMDM, an attack technique that exploits the vulnerabilities in AI models within dynamic networks. They evaluated the technique through experiments on synthetic and real-world dynamic networks. Results: The results demonstrated that GradMDM is highly effective in compromising AI models within dynamic networks. The attack successfully manipulated these models, leading to misinformation and compromised network performance. Feature and Contribution: GradMDM presents a novel attack technique that highlights the vulnerabilities of AI models in dynamic networks and necessitates the development of robust AI models.
The research focuses on investigating multi-step jailbreaking attacks on AI chatbot systems like ChatGPT. What researchers did: The researchers designed an attack mechanism that combines multiple attack techniques in sequential steps to exploit vulnerabilities in ChatGPT. They conducted experiments to assess the efficiency of these multi-step attacks. Results: The study found that multi-step jailbreaking attacks could effectively bypass ChatGPT’s security measures and extract sensitive information. It revealed a new dimension of AI chatbot vulnerabilities. Feature and Contribution: This research unveils a sophisticated attack technique on AI chatbots, signaling the need for advanced security measures in AI systems.
Each of these research papers delivers an intriguing insight into different aspects of Artificial Intelligence and networks, with a shared theme of security and vulnerability. While the first and fourth papers shed light on security breaches in search engines and chatbots, the second paper takes a detour into the medical application of AI. The third paper, on the other hand, bridges the gap by addressing the vulnerabilities of AI in dynamic networks. Together, these papers call for a unified approach in securing the diverse applications of AI and networks, ensuring integrity and confidentiality.
Written by: admin

Secure AI Weekly admin
Is this the year that AI breaks into our bank accounts? Dazed Digital, April 19, 2023 According to Alex Polyakov, the founder and CEO of Adversa AI, the security of ...


Adversa AI, Trustworthy AI Research & Advisory